I have written a lot in recent months on cyberattacks, ransomware and cyberespionage by suspected Russian, Chinese and Iranian nation state actors.
Even the US has not been spared – Edward Snowden’s 2013 disclosure of highly classifi ed National Security Agency (NSA) documents revealed the agency’s ability to tap the electronic communications of almost anyone and triggered an international boom in spyware development and deployment.
Today’s thriving international spyware industry dates back decades, but got a boost af- ter the unprecedented 2013 disclosure of highly classified NSA documents by contractor Ed- ward Snowden.
They revealed that the NSA could obtain the electronic communications of almost anyone because it had secret access to the transnational cables carrying internet traffi c world- wide and data from internet companies such as Google and giant telecommunications compa- nies such as AT&T, Sprint and others. Even US allies in Europe were shocked by the comprehensive scale of the American digital spying, and many national intelligence agen- cies set out to improve their own surveillance abilities. Private fi rms staffed with midcareer retirees from intelligence agencies saw a lucra- tive market-in-waiting free from the govern- ment regulations and oversight imposed on other industries. As with the expansion of private military contractors after the Desert Storms and re- building of Iraq and Afghanistan, cybersec rity firms specialising in government contracts saw this as market opportunity and have qui- etly expanded too.
The dramatic expansion of end-to-end en- cryption by Google, Microsoft, Facebook – WhatsApp, Apple and other major technology fi rms also prompted law enforcement and in- telligence offi cials to complain they had lost access to the communications of legitimate criminal targets.
That in turn sparked more investment in technologies, such as Pegasus, that works by targeting individual devices or smartphones. Introducing Pegasus, premium military- grade spyware, licensed by Israeli fi rm NSO Group to governments for tracking terrorists and criminals and was allegedly used in attempted and successful hacks of at least 37 smartphones belonging to journalists, human rights activists, business executives and two women close to murdered Saudi journalist Ja- mal Khashoggi, according to an investigation by The Washington Post and over 16 media partners.
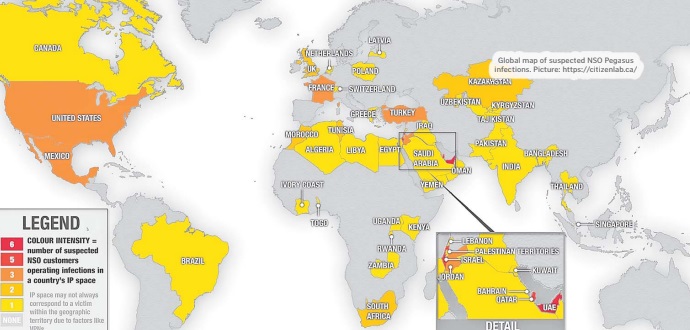
The phones appeared on a leaked list of more than 50,000 numbers that are concentrated in countries known to engage in surveillance of their citizens and also known to have been clients of the Israeli firm, NSO Group, a worldwide leader in the growing and largely unregulated private cyber spyware industry.
The list does not detail who put the numbers on it, or why, and it is unknown how many of the phones were targeted or monitored. But com- puter forensic analysis of the 37 smartphones shows that many display a tight correlation between time stamps associated with a number on the list and the initiation of surveillance, in some cases as brief as a few seconds. Forbidden Stories, a Paris-based journalism nonprofi t, and Amnesty International human rights group, had access to the list and shared it with news organisations, which did further research and analysis.
Amnesty’s Security Lab did the forensic analyses on the smartphones. The numbers on the list are unattributed, but reporters were able to identify more than 1000 people spanning more than 50 countries through research and interviews on four continents: several Arab royal family members, at least 65 business executives, 85 human rights activists, 189 journalists, and more than 600 pol- iticians and government offi cials — including cabinet ministers, diplomats, and military and security offi cers. The numbers of several heads of state and prime ministers also appeared on the list.
Among the journalists whose numbers ap- pear on the list, which dates to 2016, are report- ers working overseas for several leading news organisations, including a small number from CNN, the Associated Press, Voice of America, the New York Times, the Wall Street Journal, Bloomberg News, Le Monde in France, the Financial Times in London and Al Jazeera in Qatar.
The targeting of the 37 smartphones would appear to conflict with the stated purpose of NSO Group’s licensing of the Pegasus spyware, which the company says is intended only for use in monitoring terrorists and major criminals.
The evidence extracted from these smart- phones, revealed here for the first time, calls into question pledges by the Israeli company to screen its clients for human rights abuses. A media consortium, titled the Pegasus Project, analysed the list through interviews and forensic analysis of the phones and by comparing details with previously reported information about NSO Group. NSO Group describes its customers as 60 intelligence, military and law enforcement agencies in 40 countries, although it will not confirm the identities of any of them, citing client confidentiality obligations.
The Pegasus Project consortium found many of the phone numbers in at least 10 countries, which were subjected to deeper analysis: Azer- baijan, Bahrain, Hungary, India, Kazakhstan, Mexico, Morocco, Rwanda, Saudi Arabia and the United Arab Emirates. All 10 countries have been clients of NSO, according to consortium researchers. Shockingly, in India, the numbers of phones belonging to hundreds of journalists, activists, opposition politicians, government officials and business executives were on the list, as were numbers in several other countries in the region, including Azerbaijan, Kazakhstan and Pakistan.
Beyond the personal intrusions made possible by smartphone surveillance, the widespread use of spyware has emerged as a leading threat to democracies worldwide, many critics say. Journalists under surveillance cannot safe- ly gather sensitive news without endanger- ing themselves and their sources.
Opposition politicians cannot plot their campaign strategies without those in power anticipating their moves. Human rights workers cannot work with vulnerable people – some of whom are victims of their own governments – without exposing them to renewed abuse. This is eloquently written, potentially very nasty software in my opinion.
There’s nothing intrinsically wrong with building technologies that allows you to collect data; it’s necessary sometimes especially in times like this global pandemic. But humanity is not in a place where we can have that much power just accessible to anybody without proper rules and laws in place. Basic responsible oversight is required. In response to detailed questions from the consortium, the NSO Group said in a statement that it did not operate the spyware it licensed to clients and did not have regular access to the data they gather. The company also said its technologies have helped prevent attacks and bombings and broken up rings that traffi cked in drugs, sex and children.
“Simply put, NSO Group is on a life-saving mission, and the company will faithfully ex- ecute this mission undeterred, despite any and all continued attempts to discredit it on false grounds,” NSO said.
The NSO Group went on to state that is has good reason to believe that this list of “thou- sands of phone numbers” is not a list of num- bers targeted by governments using Pegasus, but instead may be part of a larger list of num- bers that might have been used by NSO Group customers for their own purposes.
I suppose this is possible, but if this excuse were coming from a Russian or Chinese tech company would we believe them. Pegasus was engineered a decade ago by Is- raeli excyberspies of their famed IDF Unit 8200 with government-honed skills. The Israeli Defense Ministry must approve any license to a government that wants to buy it, according to previous NSO Group statements. This high- lights my point of cyber spyware and other malware now being categorised as military weapons grade or cyber arms requiring all the necessary export licensing approvals with end- use/end user certificates by the acquiring governments!
It goes without saying that these are to be used only for lawful purposes – counter-terror- ism and criminal investigative purposes only. Lawyers from both sides would have a fi eld day, but it boils down to fundamental privacy laws and basic human rights. The technology may be advanced, but the nation’s laws exist to put these boundaries in place.
Perhaps the NSO Group is correct – they just provide the advanced technology tools for gov- ernment surveillance and monitoring. While they can screen their clients, it’s up to the in- dividual governments on how they deploy the advanced surveillance tools they have within their own countries and jurisdictions. Reminds me of that 1st century Latin phrase – “Quis custodiet ipsos custodies”? which literally translates to “who will guard the guards them- selves”?
Or as I like to paraphrase in this particular context “who will watch the watchers”? As always, God bless and stay safe in both digital and physical worlds.
ILAITIA B. TUISAWAU is a private cybersecurity consultant. The views expressed in this article are his and not necessarily shared by this newspaper. Mr Tuisawau can be contacted on ilaitia@cyberbati.com